Why ESET
ESET Technology
Trust our experience. With over 20 years engineering security software, ESET continues to be at the forefront of innovative security software design …ESET vs. the Competition
Find out what independent testing organisations compare when testing antivirus software and why they focus on those particular traits. See how ESET performs in these tests and where we excel — not to mention where the competition falls short. Check out ESET's advantage and see what makes our solutions stand out from the crowd in the global AV market.Awards
For many years ESET products have consistently been recognised by reputable, independent testing organisations as best-in-class. ESET NOD32 Antivirus has achieved the highest number of Virus Bulletin VB100 Awards, and never missed a single "In the Wild" virus
Adrian Dooley, Head of IT,
Pinewood Healthcare Ltd., Ireland
" ESET Endpoint Antivirus is peace of mind,
we don't worry about it, we don't know it's
there and it protects our business."
Bussines solutions

ESET Secure Enterprise
Safeguard the entire networkfrom endpoints to gateway server.

ESET Secure Business
Allround security for your company network,mail server and file servers

Endpoint Protection Advanced
Advanced security for the company in-houseand mobile workforce.

Endpoint Protection Standard
Essential security for company computers,mobile devices and file servers.
Individual products
ESET Endpoint Security
ESET Endpoint Antivirus
ESET Mobile Security
ESET Mail Security
ESET File Security
ESET Gateway Security
ESET Secure Authentication
ESET Collaboration
For Home

ESET Smart Security 7 for windows
Explore the opportunities online with our record breaking and fast Internet security that's easy on you. Based on the legendary NOD32, it features new technology to block malware that avoids traditional detection.

ESET NOD32 Antivirus 4 for Linux Desktop
Stop Linux malware without slowing you down. Prevent cross-platform malware attacking Windows and Apple workstations in the network.

ESET Mobile Security for Android
Explore the Internet on your smartphone or tablet. Antivirus and Anti-Phishing protect you online, while Proactive Anti-Theft protects your missing device. SMS & Call Filter helps you manage your calls.

ESET Cyber Security Pro
ESET Cyber Security Pro
ERP Products
LOGO ERP solutions are used by several firms both in Turkey and around the world. Our ERP solutions enable tracking and managing critical administration functions from procurement chain to finance processes in an effective manner.
Tiger Plus products – developed based on the requirements of middle and large scale of enterprises that engage in trading and service fields – helps managing business processes effectively. Enterprises having a need of sector-oriented requirements can also benefit from the advantages of an effective and agile ERP solution by LOGO Java Solution. Furthermore, enterprises engage in planning, production, quality control processes can manage their procurement chain, cost management and quality control processes by integrating with Tiger Enterprise.
Tiger Enterprise

Expert's Choice
Tiger Enterprise is an ERP software developed for middle and large scale enterprises tracking in-house business processes and analyzing results in detail through purchasing, production and distribution features and other basic activities supported by planning, finance and human resources management.Always one step ahead with Tiger Enterprise…
Tiger Enterprise optimizes in-house processes with planning, finance and human resources managing purchasing, production and sales logistics, and it increases your efficiency in supplier and customer relations.Why to Choose Tiger Enterprise?
- Adopted quickly in company processes,
- Supports multi-dimensional planning and control for companies working in more than one location,
- Performs data exchange with external systems easily,
- Open to innovation and development, easy to customize according to user needs,
- High performance in increasing operational and data load,
- Meets all kinds of needs thanks to its local and extensive business partnership structure,
- Integrable with software products developed by other companies,
- Supports modular structure in line with needs and requirements,
- Designs different reports for different user needs thanks to flexible reporting features,
- Foreign language and reporting support for companies engage in export/import and other international firms,
- Ease-to-use with interface standard,
- History records of all transactions and operations,
- Usable on internet, supports mobile technologies,
- Has a full command of legislation and business rules.
LOGO Human Resources

LOGO Human Resources optimizes human resources management processes with comprehensive product features and customizable and flexible structure, reduces workload of human resources department and leads managers in tactical and strategic decisions by presenting various analyses.
Why Choose LOGO Human Resources?
LOGO Human Resources has a modules structure and offers a wide range of solutions including salary, debit/credit, performance, career, training and vacation management, recruitment management, organizational planning, wage simulation, survey management and payroll modules.Corporations can use Employment Management as a single module or enrich their application by adding new modules and switch to Human Resources gradually.
Modules
- Employment Management
- Organizational Planning
- Training Management
- Recruitment System
- Survey Management
- Performance Management
- Career Management
- Time Planning
- Wage Simulation
- Employment Management
- HR Web
Tiger Plus

Here presents the best ERP software complying with international standards and conditions in Turkey: Tiger Plus
Tiger Plus is an ERP solution
- Supporting corporate and operational strategies of companies,
- Fully compatible with corporation
- Providing competative advantages both in domestic and foreign market
- Supporting growth process fully
Tiger Plus is offering new insights to competitive companies by reinterpreting the ERP concept. Furthermore, this application software provides solutions to corporations and groups engaging in sales, distribution, production and service fields in all industries at a minimum cost.
Why Choose Tiger Plus
- Removes document and phone traffic by performing approval and control of work flow and processes in electronic
- Automate your reports and tasks performed frequently by scheduling and running them whenever required. Tiger Plus reminds your work list and informs the relevant person when it is complete.
- Complies with Turkish Commercial Code and other standard local/international accounting & finance standards (FAS52, IAS, IFRS)
- "Object Designer and LOGO Objects" customizing tools developed to create new functional customizations in line with the corporate requirements, exclusively for LOGO Solution Partners
- Helps in making several adjustments on reports such as color, font and more visual changes, use drawings and graphics for company logo, delete columns or add fields to columns, and create different queries by defining new filters.
- Tracks top selling and purchased products, the most purchasing AR/APs and the products purchased by them, stock/purchase turnover, bank and safe deposit status and more over a single widow with Manager Dashboard
- Finds documents of records and transactions defined with "Document Management" function under the relevant catalogs you defined.
Other Features
- Open and Flexible Structure, Relational Database Support - MS SQL and Oracle
- Multiple language support
- Web use with WebTIGER
- E-business bridge between corporations and other firms and banks thanks to LogoConnect
- Integrated structure with e-mail systems
- Smart document integration with MS Office
- More than 200 integrated business applications developed by LOGO Solution Partners
- Fully-compatible with Windows interface standards
24/7 access to your desktop. Because the unexpected happens all the time.
One simple tap on your mobile device, and you're connected reliably to your computer. Or access it from any other computer through a browser and your secure Parallels account. Navigate your hard drive easily to find a file or photo, then copy or open it with a tap .


Parallels Access
Access to your computer anywhere, anytime
Introduction to Parallels Desktop 11 for Mac
- NEW! Pro Edition
- NEW & COOL! Cortana for your Mac
- Run Windows 10, Windows 8, Windows 7, and more
- NEW! Ready for OS X El Captain
- Powerful performance
- Mac gestures work in Windows
- View Full Details
- Need Business Licensing?

Parallels Mac Management
for Microsoft SCCM
- Best remote access to your PC or Mac
- For iPhone, iPad, and Android devices
- Use desktop apps like they were made for your device
- NEW! File sharing
- NEW! Apple Watch support
- View Full Details
- Need Business Licensing?
Parallels Remote Application Server Demo

Parallels Transporter
Move all your Windows files from your PC to your Mac
- Extend SCCM to manage Macs
- Network discovery and auto enrollment
- Deploy pre-built OS X images
- Deploy OS X Configuration Profiles
- Application Portal for Macs
- Deploy and manage Parallels Desktop & Windows
- View Full Details
Parallels Mobile Device Management Demo

Parallels Desktop 11 for Mac
Run Windows on your Mac
Parallels Transporter Tutorial
- Move all your files from your PC to Mac
- Move browser favorites and bookmarks
- No need for new software when you switch
- All your stuff works on your Mac, using Parallels Desktop for Mac
- View Full Details

Parallels Remote Application Server
Managed, secured access to your desktops, data, and applications
Reduce costs
Value your investment
Effortless client management
View Full Details

Parallels Mobile Device Management
Mass Manage Mobile Devices
Remote Lock & Wipe
Track Android and iOS Devices
Mass Deploy Apps To Groups Of Devices
View Full Details
Denyall
To use a domestic metaphor, detecting IT vulnerabilities and filtering incoming Web traffic is the equivalent to keeping doors and windows closed, controlling who knocks on the door and making sure people don't misbehave once they are inside your home. DenyAll products are designed to perform these detection and protection duties. The DenyAll Application Security Platform (DASP) is the foundation of all DenyAll products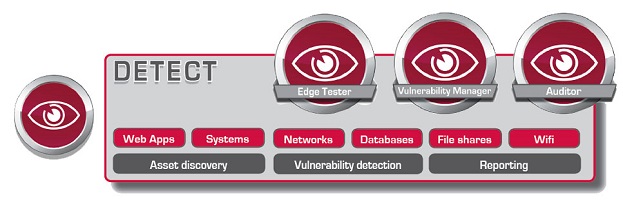
DenyAll vulnerability scanners are designed to help auditors, IT and security tems assess the security of their IT infrastructure, including applications. This can be done internally, using a virtual machine, a portable scanner for remote sites, or in SaaS mode, from the cloud, to test the defenses from the outside.
DenyAll's web application & services firewalls leverage a time-tested reverse proxy and modular architecture to defend IT infrastructures against known and unknown application-layer attacks. Unique innovative features include the Scoring List, User Behavior Tracking, Multi-DMZ architecture, Pooling Mode, Client Shield, JSON security engine and the Secure Transparent Mode, for easier deployment without compromising security.

Reducing the total cost of ownership, fostering internal cooperation among application, infrastructure and security administrators is the mission of the DenyAll Management Console (DAMC) and Application Security Dashboard. Both will agregate events from the Detect and Protect family of products to deliver superior application security intelligence.
Product
DenyAll's product offering To fight againts modern attacks, which tend to target the application-layer of any IT infrastructure by default, a simple but efficient strategy calls for filtering Web traffic, to block application-layer attacks, and to reduce the attack surface by proactively managing the infrastructure's vulnerabilities. This is the purpose of DenyAll's three product lines: to detect security weaknesses, to protect the application layer and to manage the process, with a view to improve over time your application security.
Detect
The vulnerability scanners in this family of products was designed to reduce the potential attack surface, by proactively managing vulnerabilities at the network, system and application-layers .Manage
DenyAll's Management Console, combined with the Application Security Dashboard enable organizations to better control their application security policy, while reducing operational costs.Detect
DenyAll's Web Application Firewall product range meets the needs of organizations of all sizes and level of requirement, from plug & play to next generation WAF .Technologies
DenyAll's product offering
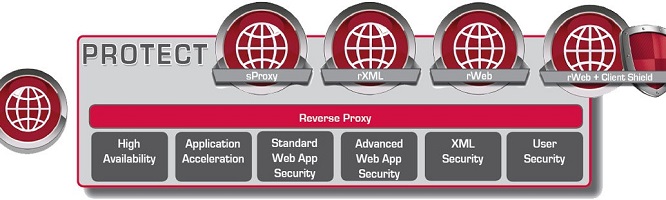
To fight againts modern attacks, which tend to target the application-layer of any IT infrastructure by default, a simple but efficient strategy calls for filtering Web traffic, to block application-layer attacks, and to reduce the attack surface by proactively managing the infrastructure's vulnerabilities. This is the purpose of DenyAll's three product lines: to detect security weaknesses, to protect the application layer and to manage the process, with a view to improve over time your application security.Reverse proxy, secure architecture
Protocol break and canonization ensure a first level of protection. Multi-DMZ architectures and the pooling mode further increase securityAcceleration and load balancing
Acceleration, caching, TCP multiplexing and load balancing ensure an imperceptible impact of the security functions on the users' experienceHigh availability
In active-passive mode or active-active mode, on several nodes, the clustering technology ensures the application infrastructure keep performing at all timesStandard Web Security
The black list blocks known attacks while the scoring list's weighting technology will stop yet to be discovered (0 day) attacksAdvanced Web Security
The white list, stateful analysis of session information (cookies, cache) and User Behavior Tracking modules block brute force and denial of service attacksUser Security
Management of client certificates, authentication and integration with Single Sign On tools ease the user experience and increase securityBrowser Security
The Client Shield module, an rWeb option, controls the safe execution of connecting browsers, thus preventing man-in-the-browser attacksPhysical and virtual appliances
DenyAll's products can be acquired as physical appliance bundles or virtual appliances, in addition to traditional software packagesSolutions
Proven solutions, deployed by demanding customers
Since 2011, DenyAll's products have protected the consultation and transaction sites of numerous banks, as well as e-commerce sites, defending them against data theft in accordance with the PCI DSS standard. Companies of all sizes protect the Web front ends of SAP and Oracle applications, critical Web Services-based applications, Webmail access (Outlook Web Access, iNotes), and collaboration tools (Sharepoint).eBanking
The security of B2C applications is a major concern. However, banks and insurance companies place equal importance on performance and compliance with standards.eAdministration
Main challenges: to facilitate the exchange of electronic data without sacrificing the confidentiality of individual data, and to ensure service continuity.eCommerce
It is simply unacceptable for an application that generates sales to be unavailable or to reveal client bank card numbers.PCI DSS
To find out how to ensure application compliance with PCI DSS (Payment Card Industry Data Security Standard), consult the associated micro-site.Web Services
Interconnecting Web applications and automating exchanges with subsidiaries, partners and suppliers require tailored security solutions.SAP
SAP NetWeaver portals, and behind them what are sometimes critical enterprise applications (ERP, RH, CRM, etc.), are vulnerable to attack. You need a WAF!Sharepoint
Collaborative working and data sharing are booming. These new types of usage are based on low-security Web protocols. Watch out for data loss!Webmail
E-mail has become a critical application. Opening up access to mobile employees and new form factors is not without risk.Virtual Patching
What is Virtual Patching? What are the challenges of virtual patching in support of your application security policy?Datasheets
DenyAll Detect Products
Download here the DenyAll Detect products datasheets. The DenyAll Detect range products is composed of: Edge Tester (SaaS), Vulnerability Manager (virtual machine) and Auditor (USB). The DenyAll Detect products range are vulnerability scanners.DenyAll Protect Products
Download here the DenyAll Protect products datasheets. The DenyAll Protect range products is composed of: sProxy, rXML, rWeb and rWeb + Client Shield. The DenyAll Protect products range are Web Application Firewalls (WAFs).DAMC 4.0
The effectiveness of an application security policy depends not only on the quality of the WAFs used, but also on the tools made availa¬ble to the team responsible for defining and deploying it. DAMC gives you the tools to cen¬trally manage a global policy adapted to your risks, delegate certain administrative tasks to the teams responsible for local implemen¬tation, and consolidate the reports necessary for good governance of your security policy.Appliances
The new DenyAll range of appliances offers price/performance choice that meet the IT needs of small and large companies. Performance capacities can be upgraded at a software and hardware level thanks to enhanced scalability.Gartner Magic Quadrant for Enterprise Information Archiving
According to Gartner: "Retain's administrative and compliance interface is easy to use for both administrators and compliance personnel and GWAVA's ability to handle almost any messaging data type allows for a centralized messaging data compliance experience. Retain allows for easy search and e-discovery across multiple outside data sources not held within the archive repository.
Unified Archiving
Retain provides multi-platform unified message archiving of all email, social media, IM and mobile communication data for case assessment, search, and eDiscovery and can be deployed on-prem or in the cloud.
Messaging Security
The GWAVA secure message gateway uses the latest technology to detect viruses, malware, spam, and illicit images and block them from your system. Anti-Spam Protection — GWAVA provides multi-layer spam defense to protect email and keep unwanted traffic off your collaboration system.
GWAVA solutions include:
Email Messaging Security:
GWAVA has engineered antivirus and anti-spam protection specifically for maximum protection of today's vast and complex email systems and servers. A measure of the power of GWAVA comes from its swift ability to stop illicit and pornographic images using Image Analyzer. Furthermore, GWAVA protects the SMTP from DOS and DDOS attack—all this while securing company networks with web traffic and content filtering. GWAVA integrates with compatible ICAP systems to monitor, filter and block incoming and outgoing traffic. This keeps organizations safe from malicious, inappropriate or time-sucking content and websites. And these features deploy as seamlessly in SMBs as they do in the world's largest and most security-intensive environments.Unified Archiving: Archiving Across Mixed and Multiple Platforms Environments
Platforms such as Microsoft Exchange, Novell GroupWise, Office 365, live@edu, and Gmail pose unique challenges when it comes to successfully managing an integrated system. GWAVA Retain provides top-notch performance in companies that run multiple email applications (e.g., a combination of GroupWise and Exchange); Retain executes with precision in these mixed-platform environments. This is why we use the word 'unified' when describing the way in which system administrators effectively manage separate systems with GWAVA Retain. Administrators archive from one console, using one login, all using proven GWAVA technologies.Social Media and Mobile Archiving
In today's ultra-connected world employees, at dramatic rates, are tapping into social media while at work, or via company-owned devices. Employee access to Facebook, Twitter and other internet applications demand leading-edge solutions which assure that company assets and data are kept airtight and secure. GWAVA Retain is the best-of-breed solution for managing employee social media usage on corporate devices, whether that device is in the office or off the network. And when it comes to mobile, Retain provides peace of mind for organizations with corporate or BYOD smartphone users and admins by safeguarding against security breaches with powerful archiving, searching and eDiscovery of text messages (MMS, SMS, BBM), instant messages, and phone logs. Archived social media content, along with email archive, can be accessed from one central databasing. This unified archive allows for quick and easy access and eDiscovery of all archived data from console.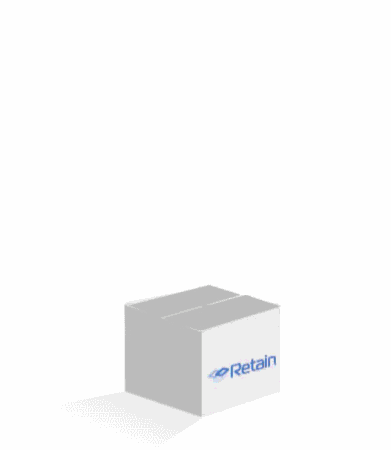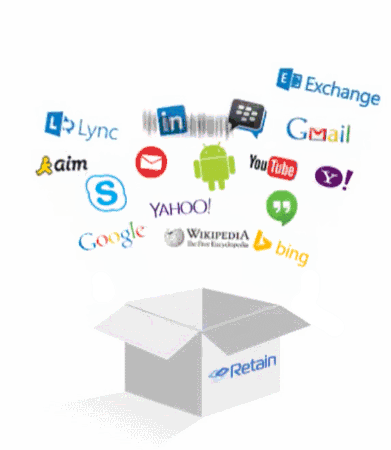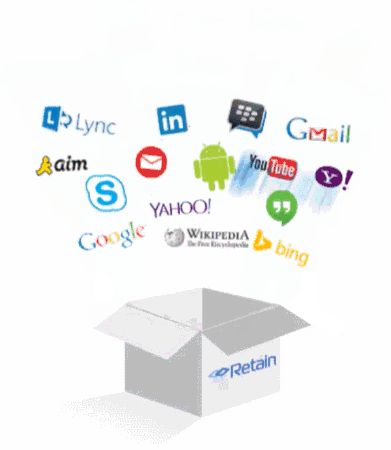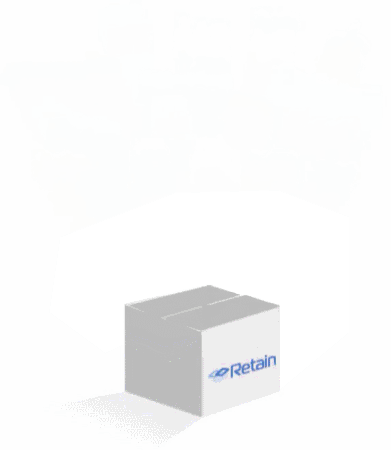
GWAVA: The Benefit to Your Organization :
GWAVA is unsurpassed at protecting email. GWAVA is unparalleled at providing unified archiving and critical messaging security—all this while reducing costs, managing complexity and mitigating risk. With offices worldwide, GWAVA delivers support for thousands of customers globally. This commitment to clients reflects the GWAVA assurance to customer satisfaction: Satisfaction with our software, our service and our entire line of products. This is the commitment that GWAVA is proud to uphold.GWAVA offers an array of products and services to its customers:
1-Retain Unified Archiving2-Retain for Exchange
3-Retain for GroupWise
4-Retain Social
5-Retain Cloud Archiving
6-Retain Mobile
7-Retain for BlackBerry
8-GWAVA Messaging Security
9-Reload Business Continuity
10-Blueprint for Reload
11-Reveal Email Forensics
12-Redline System Reporting
13-Vertigo Mailbox Management
